What is Just-In-Time Access?
A network administrator often needs to grant access permissions to users who only require temporary access. Take the example of a short-term contractor, who is working with your organization to troubleshoot some issues in your data center environment.
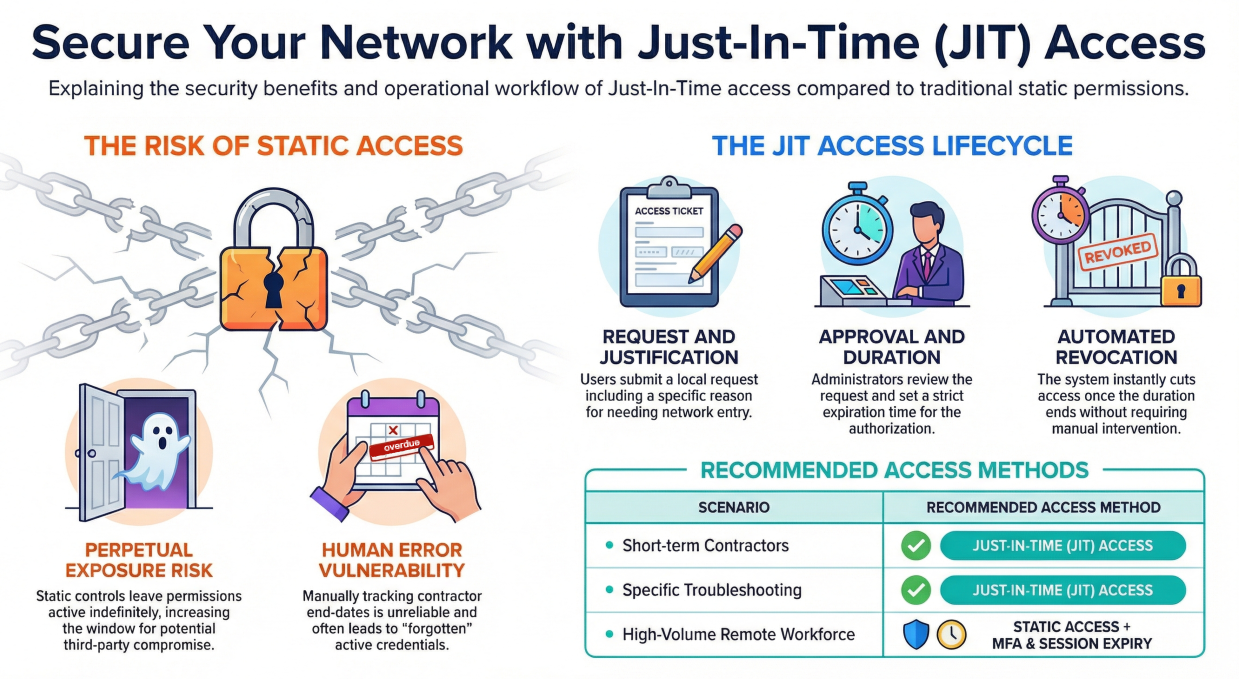
In a traditional workflow, the administrator will set this contractor up as a user in their system, and set access controls to give them the necessary permissions on the network to reach resources in the data center. However, these permissions are static. Until the administrator changes these access controls or removes the user, they have constant permission to access the destination.
This is inherently insecure for two reasons. For one, it requires the administrator to keep track of this contractor. They might need to set up some form of notification for when the contractor’s job is done, check in to confirm, and then apply the necessary changes. This introduces the possibility of human error.
Additionally, consider that this contractor may only need occasional access, like for a set two hour time period weekly. With static access controls, they retain privileged access for the entirety of their time with the company. This can inadvertently expose these privileges to third parties via compromise, when it is completely unnecessary.
Just-in-Time Access, or JIT for short, resolves these issues in a way that is inherently secure. Quite simply, a user requests access, and an administrator reviews and approves the request, setting a duration for access. At the end of this duration, authorization is automatically revoked.
This system aligns with the principle of least privileged access under the Zero Trust framework. It removes many of the potential vulnerabilities in a standard system, and minimizes the threat of malicious third party actors to a miniscule footprint.
JIT usually functions via an automated system including approval workflows, to simplify the process:
- Users request access locally, and must provide a justification for their request.
- Administrators receive notification of the request and review, making the decision to approve or deny access, and setting a reasonable duration for authorization.
- Upon approval, the system automatically grants immediate access to the user.
- At the end of the grant period, access is automatically revoked.
- Once the grant period has ended, the user can submit another request for access.
Where Just-in-Time Access does not make sense
In an ideal world, every user would have approved access to specific resources for only the necessary timeframe. However, consider an organization with hundreds of remote workers who need access to the office network.
In this scenario, if you have implemented JIT Access, your administrators will quickly become overwhelmed, and your workers would quickly become both extremely unsatisfied and unproductive. It’s easy to see why.
Imagine your network administrators receiving hundreds of requests for access on a daily basis, and having to approve each one on a case-by-case basis. They might spend their entire day reviewing requests. Likewise, as the queue builds up, users would be waiting longer and longer to get the access they need.
In such a scenario, static access becomes necessary.
However, that doesn’t mean there is nothing you can do. Access Controls can still minimize exposure to risk by limiting what each user can access within the network. MFA with session expiry will ensure that access does expire, and that the user must reconfirm their identity on a regular basis to maintain access. It just doesn’t require the manual approval step.
SCIM integration can further simplify and automate the process of adding, removing, and updating users, and setting permissions, so that network administrators are not responsible for monitoring and managing individuals’ access.
Other functionalities like posture checks and device approvals can provide additional layers of security. Combined, these functionalities provide your organization with a great zero trust security model.
How Netmaker Implements Just-in-Time Access
Netmaker provides JIT Access as a part of its Enterprise version. This optionally-enabled functionality works according to the standardized methodology:
- User requests access, providing justification
- Administrators are notified
- Administrators review, approve or deny, and set an access duration
- User receives immediate access for the specified time period
- Access is automatically revoked at the end of the duration
- Access can be requested again as necessary
Netmaker understands that JIT is not the right fit for every scenario, which is why it can be optionally enabled for specific use cases. For other use cases, standard access control methods can be used, combined with MFA, session expiry, SCIM integration, posture checks, and a whole host of other functionalities that maximize security and minimize risk under a Zero Trust framework.
Different use cases can be managed separately under one Netmaker implementation, so you can implement JIT for your short term contractors, and implement Zero Trust Network Access for your remote employees.
Learn More
If you’re interested in learning more about how Netmaker implements JIT Access and Zero Trust, you can contact our team here. We’d be happy to walk you through best practices and help guide you on your mission to improve network security at your organization.
.svg)







.svg)