Enhancing Cluster Connectivity with the Netmaker Kubernetes Operator

🛠️ Enhancing Kubernetes Connectivity with the Netmaker Operator
Managing Kubernetes networking can present significant infrastructure challenges, particularly when dealing with private clusters and complex cross-cluster connectivity. Providing secure network access outside of a cluster often requires intricate configurations that can burden administrators.
The Netmaker Operator for Kubernetes, a new open source project from Netmaker, addresses these challenges by simplifying inbound access to services and the Kubernetes API, while also facilitating outbound connectivity to external resources.
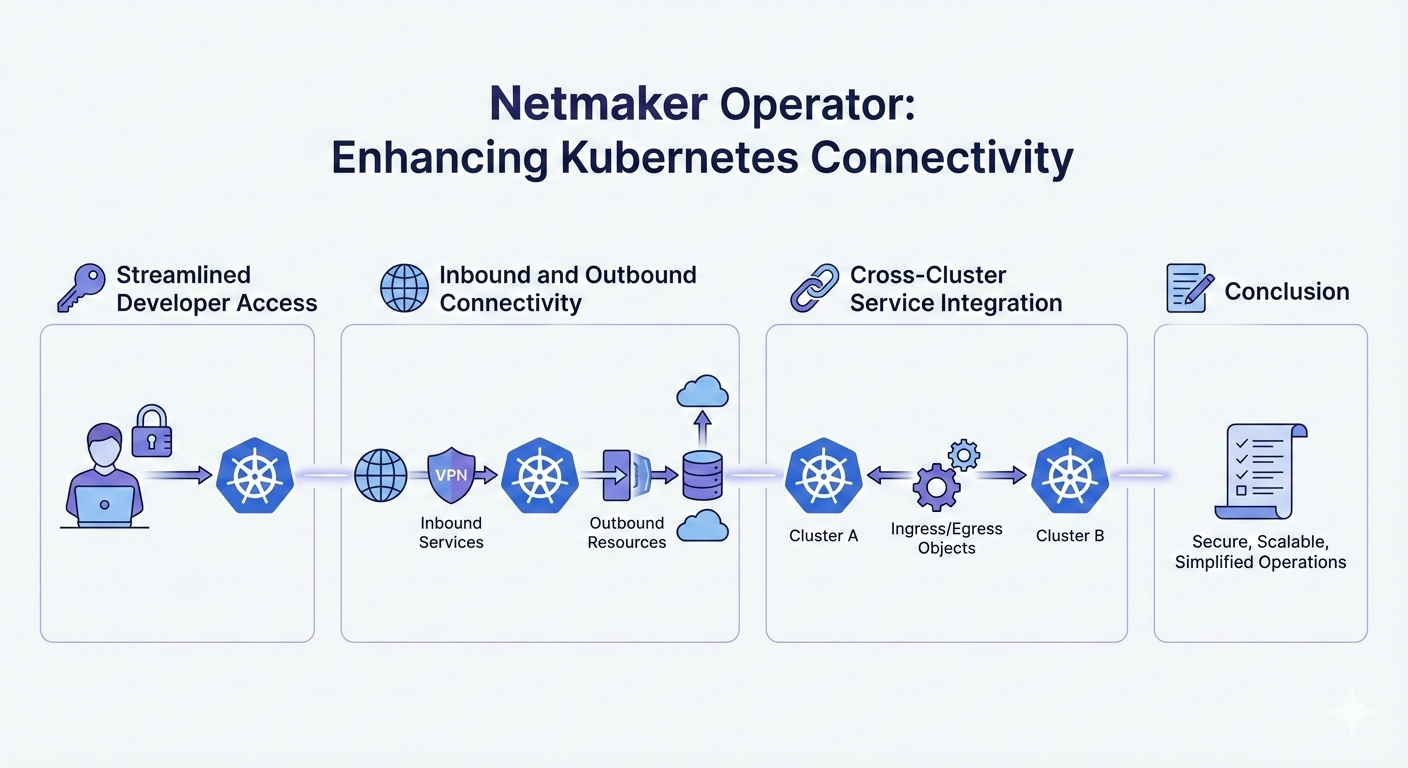
The Netmaker Operator provides four core networking capabilities designed to streamline operations:
- Integrated Cluster Access: Simplifies and secures kubectl access for developers.
- Inbound Service Access: Enables secure access to internal cluster services.
- Outbound Service Access: Connects cluster workloads to external resources like databases, VMs, and entire private LANs.
- Cross-Cluster Connectivity: Bridges services across geographically or logically separated clusters.
🔑 Streamlined Developer Access
The Netmaker Operator allows developers to execute kubectl commands over a secure, private connection to the cluster. Implementation follows a standard four-step workflow:
- Define RBAC Groups: Utilize existing Kubernetes Role-Based Access Control (RBAC) configurations or define new groups specifically for cluster access.
- Synchronize with Netmaker: Ensure group names in Netmaker match those in Kubernetes. This process is automated if an Identity Provider (IDP) is integrated with Netmaker.
- Activate Network Access: Users authenticate via the client application to enable their connection.
- Configure Endpoints: Developers point their kubeconfig to the secure cluster endpoint designated by Netmaker.
This approach provides a secure, unified entry point for private cluster operations, adding a level of security to cluster operations and simplifying access to private clusters.
🌐 Inbound Access to Private Services
While traditional service access often requires Ingress objects accessible over a public network, or complicated service meshes, the Netmaker Operator utilizes custom objects to expose private services directly over a VPN. By deploying a Customized Service Object, administrators can define specific parameters for external access. Authorized users can then reach these services via private IP or DNS. Simply:
- Deploy a Custom Service Object: Deploy a service object with the Netmaker annotations in the target namespace.
- Grant Access to Your Users: Within the Netmaker platform, define who can access the service using RBACs and ACLs.
Your users can now access workloads on Kubernetes without having to expose them to the internet.
🌐 Outbound Access to External Resources from Cluster Workloads
Resources outside of your Kubernetes cluster are typically only accessible when exposed over a public network, or when deployed in the same local network as the cluster itself. This can make accessing private resources like databases, VMs, or edge devices very difficult. The Netmaker Operator facilitates outbound access to private resources outside of your cluster over a secure network with an easily deployed custom object:
- Set up Netmaker Access: Deploy a Netmaker endpoint in the target environment, and optionally configure traffic forwarding to a local network.
- Deploy an Egress Service Object: Create a custom object within the cluster that defines what external resource is now accessible over the private network.
Your workloads on Kubernetes can now access the private resource outside of your cluster easily and securely.
🔗 Cross-Cluster Service Integration
By deploying both Ingress and Egress Service Objects, organizations can establish seamless connectivity between disparate Kubernetes clusters. Defining an Egress Service Object makes a cluster service reachable over the private network, while an Ingress Service Object makes a private cluster service available to the network. To enable Cluster B to access a service residing on Cluster A, administrators simply:
- Deploy an Ingress object on Cluster A for the service.
- Deploy an Egress object on Cluster B for the service.
Cluster B can then access the service on Cluster A, a model that can be applied to any number of services in either direction.
📝 The TL;DR
The Netmaker Operator represents a significant advancement in Kubernetes networking, transforming how teams manage complex connectivity requirements. By abstracting the difficulties of private cluster access and multi-cluster communication into manageable custom objects, it allows engineers to focus on application delivery rather than network troubleshooting. Whether securing developer workflows or bridging hybrid cloud environments, Netmaker provides a robust framework for modern, scalable, and secure infrastructure.
You can find the operator here.
.svg)







.svg)